Cloud computing security is an issue that sparks great debate among tech professionals. Some think the cloud is inherently secure, in fact even more than data centers. Others think clouds are not inherently secure, and so are determined to never use them for mission critical workloads.
In truth, cloud environments can be more secure than data centers or less secure than data centers, depending on how they are implemented. Organizations that are serious about cloud security should endeavor to know the details of what cloud companies offer because it’s necessary to effect sound cloud security management.
Cloud Storage and Backup Benefits
Protecting your company’s data is critical. Cloud storage with automated backup is scalable, flexible and provides peace of mind. Cobalt Iron’s enterprise-grade backup and recovery solution is known for its hands-free automation and reliability, at a lower cost. Cloud backup that just works.
The bottom line: Cloud security should be top of mind for organizations because their reputations, operations, and financial security depend on it.
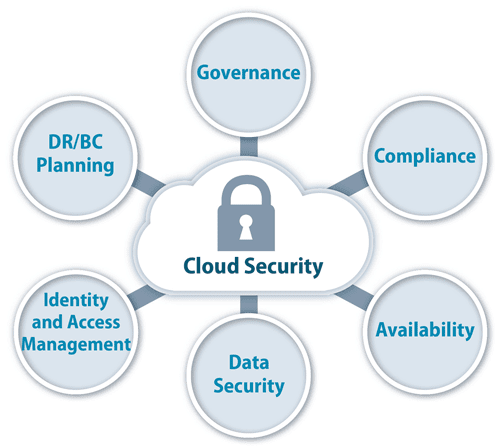
What is Cloud Security?
In brief, cloud security is comprised of two main factors:
- Cloud security is a set of company-created guidelines to block any possible form of data loss, breech, or unavailability.
- Cloud security is also a specialized, add-on cloud service that ensures cloud environments and the data stored in them are secure.
Is the Cloud Secure?
Cloud providers and security companies wouldn’t survive long if they weren’t able to protect their customers’ data well. However, organizations must decide for themselves which security features they require, and these may not be a one-size-fits-all proposition.
For example, basic cloud services tend to include basic security features; however, enterprises require enterprise-grade security options.
When moving to the cloud, security and IT professionals are wise to understand their company’s risk appetite and security posture so they know what cloud-based controls will be necessary. For example:
- Regulatory compliance may be necessary. If so, the organization will want compliance controls.
- The effectiveness of the data security required should be verifiable.
- Cloud-based controls should be at least as robust on-premises controls.
- The cloud provider should have physical security in place to ensure that bad actors do not have access to equipment.
To put customers’ minds at ease, cloud providers offer management consoles IT and security professionals can use to ensure that:
- Their data and the cloud environment that hosts it are secure.
- They have up-to-the-minute insight into the current state of security.
- They receive timely notifications of out-of-bounds conditions and noteworthy events.
- They can identify the root cause of issues and remediate them.
Given the rapid growth of data volumes, the accelerating pace of technology innovation and constantly emerging black hat tactics, relying on the security of your cloud is a reasonable option. This is because – if managed properly – it can provide greater resilience and security than in-house data centers. To realize that, however, cloud security management and security management should be aligned and consistent.
Though cloud security is complex, these three guidelines provide a solid starting point.
Security Issues in Cloud Computing
As noted, the cloud can be more secure than data centers, but one is not inherently more secure than the other. The difference depends on the enterprise’s own security practices. For example, it’s entirely possible to misconfigure virtual assets in the cloud in a way that causes security vulnerabilities – even though the company subscribes to a cloud security option. That’s why IT and security teams should have a solid understanding of cloud computing challenges.
Unlike traditional network environments which attempted to protect a company using perimeter defenses such as firewalls, cloud environments are inherently connected to third-party environments which may include compromised application programming interfaces (APIs) and access controls that have not been properly set and managed.
In addition, different types of cloud environments also represent unique challenges. For example:
Private Cloud
A private cloud typically resides within a data center, so the company owns and manages all the hardware and software. Any weaknesses in security practices that already exist in data center security may carry over to the private cloud. Admins must understand the difference between cloud and on-premise software: on-premise software is all yours to manage, while cloud software is managed by someone else. Yet neither one can be “set it and forget it.” Both must be managed.
Public Cloud
Public clouds have a multi-tenant architecture, which means you share computing or storage resources with others. Granted, the cloud provider has set up virtual barriers that separate your cloud environment from another customer’s environment. Still there could be data corruption.
In addition, the cloud provider’s terms of use require users to contractually agree to refrain from doing anything that could adversely affect other customers, but not everyone will always honor that commitment. In addition to the possibility of malicious actors, an innocent neighbor could do something inadvertently that enables a bad outcome such as a distributed denial of service (DDoS) attack.
Hybrid Cloud
Most organizations have hybrid clouds which involves some combination of data center, public cloud, and/or private cloud. The risk here is having different security strategies for the different environments which, in effect, is having three different security policies that are difficult to manage and reconcile. Also, staffers sometimes forget that there are connection points between or among the various physical and virtual assets which serve as vulnerability points.
Multicloud
Most organizations also have a multicloud strategy, which tends to mean they are using more than one type of public cloud service provider. The two most popular mulitcloud options are Amazon Web Services and Microsoft Azure. In this case, one should fully understand the security features each offers.
True cloud security requires integrating a cloud security policy throughout your entire system.
Cloud Security Architecture
Cloud security architecture impacts the effectiveness of cloud security. The following are a few actionable security management tips you can use to fortify your cloud environment.
Prevent
The “best” kind of cyberattacks are those that fail from the beginning. The best way to prevent an attack is to continuously:
- Identify vulnerabilities.
- Prioritize them based on their severity, threat intelligence, and the assets that would be affected by the attack.
- Remediate the prioritized vulnerabilities by patching them.
Unfortunately, most organizations are not managing security vulnerabilities as continuously as they should. Instead, they’re managing vulnerabilities on a periodic basis, such as Patch Tuesday, monthly, etc. Most organizations also struggle to prioritize vulnerabilities because they can be so numerous.
Detect
Vigilance is one of the best security defenses. Organization should have detection controls in place that identify issues and alert security personnel when necessary. Detection controls tend to work in tandem with correction controls that may be automatic, manual, or a combination of the two, depending on whether the situation is caused by a minor error, a cyberattack, or other type of incident.
Correct
Security incidents happen no matter what security controls are in place. Before they happen, there should be correction controls in place that minimize the amount of damage a bad actor can cause. For example, if a hacker gains access to a database or sensitive file, what happens next? If the data are destroyed, are there disaster recovery options in place?
Cloud Security Software and Services
The following are some of the cloud security software and service options businesses should consider:
- IaaS or PaaS cloud security options – these are add-on services that provide enterprises with more extensive security options than are available with basic cloud options.
- Identity and Access Management (IAM) – these tools ensure that only authorized parties have access to data and computing resources.
- Physical security – IaaS/PaaS providers should have physical security – locked door, checkpoints – in addition to digital security to ensure their IT assets remain secure.
- Encryption – encrypts data at rest and in motion.
- Penetration testing – outside consultants are hired as “white hats” to break into a company’s system with the goal of identifying weaknesses.
- Compliance controls – ensure adherence to HIPPA, GDPR, etc.