Cloud compliance ensures that cloud computing services meet the compliance requirements of enterprise customers. However, enterprises adopting cloud services should not assume that every cloud company necessarily meets the organization’s unique requirements because compliance-related service offerings vary.
Data transfer, storage, backup, retrieval, and access necessitate cloud compliance. While IT tends to be in charge of implementing compliance, other functions or formal departments may (and probably should) be involved. This involvement includes decision-making, monitoring and audits, governance, security, data protection, risk management and legal.
Cloud Storage and Backup Benefits
Protecting your company’s data is critical. Cloud storage with automated backup is scalable, flexible and provides peace of mind. Cobalt Iron’s enterprise-grade backup and recovery solution is known for its hands-free automation and reliability, at a lower cost. Cloud backup that just works.
Compliance is a very serious topic that should be understood in considerable depth, since compliance failures can lead to regulatory fines, lawsuits, cybersecurity incidents and reputational damage. It is therefore important to understand the details of what your cloud provider offers and what your company requires.
This article provides an overview of cloud compliance considerations and lists some of the services that are common among the top three service providers, Amazon Web Services, Microsoft Azure and Google Cloud. Organizations interested in procuring cloud compliance services should visit the respective service providers’ websites for the most up-to-date information.
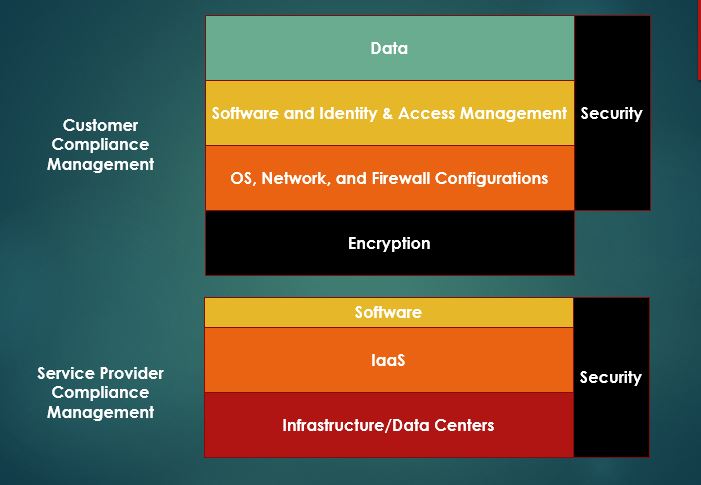
Cloud compliance issues include both customer compliance and service compliance management.
Cloud Compliance Checklist
One of the first concerns that arises when one considers cloud compliance is the fact that the customer is not managing its own infrastructure.
Should something go wrong, raising outsourcing as a defense won’t work. In fact, cloud providers, including AWS and Microsoft Azure underscore the fact that cloud compliance is a dual responsibility. Yes, they have a level of contractual responsibility to customers, but customers have to look out for their own best interests. This includes choosing the right set of services for the customer’s requirements, handling customer-controlled configurations properly, etc.
Some other considerations for ensuring cloud compliance include:
- Data. Decide what will be and will not be stored in the cloud and why.
- Data location. Auditors may ask where data is located, but your cloud service provider may not reveal that information.
- Asset management. The cloud service provider is responsible for managing its infrastructure assets, you are responsible for managing your company’s assets, including hosted operating systems and applications.
- System and data access controls. Compliance tends to involve data security. You should understand who at your company has access to what and who at your cloud service provider, including third-party contractors, has access to what.
- Configuration management. If you misconfigure an AWS S3 bucket, for example, you bear the sole responsibility for the mistake.
- Data encryption. Staying compliant usually means encrypting data at rest and in motion to protect it.
- Shared or private resources. Depending on your company’s specific compliance requirements, you may require a private data center suite in the cloud service provider’s data center.
- Service Level Agreement (SLA). The laws and regulations that apply to your company may have service level agreement requirements. That may limit the types of services your company can use.
- Data protection. It is important to understand the degree to which a cloud provider will protect your information.
- Compliance Certifications and Legally Accepted Substitutes. Not all cloud compliance services are capable of being certified. If certification is not possible for whatever reason, the cloud provider may find a way to be compliant such as adhering to a stricter set of standards.
- Auditors. Understand which third parties audit cloud compliance and read the reports. Also understand whether your company will be entitled to audit cloud compliance.
- Incident response. Understand the scope of potential incidents and what sorts of incident response are in place should those types of incidents arise (e.g., receiving alerts and how quickly).
- E-discovery capabilities. This is a legal issue rather than a regulatory issue. If your company finds itself in any type of litigation, you’re going to want fast access to the requested data and only the requested data.
- Security requirements. You should understand what forms of security your company requires to choose the right cloud services generally. For compliance purposes, you need to understand what level of security a law or regulation requires.
- Disaster recovery. Outages happen. The laws and regulations that apply to your company may have specific disaster recovery requirements.
- Due diligence. Understand how periodic due diligence will be handled.
- Informational resources. The informational resources cloud service providers offer varies significantly. The ones that provide a lot of information do so to help customers succeed with cloud compliance from the get-go.
- Compliance reports. Understand the scope of compliance reports customers can access and read them.
What a Cloud Compliance Service Provider Might Cover
Different cloud service providers present their cloud compliance services differently. Some providers use lists while others use grids. Some break things out into categories while others do not.
For example, AWS has three lists that cover certifications/attestations; laws/regulations/privacy; and alignments/frameworks. Microsoft and Google prefer grid UX elements. In addition, Microsoft breaks out its compliance services into global, government, industry, and regional.
Since the presentation of the information differs from service provider to service provider, customers should review offerings carefully. Assumptions are dangerous when it comes to compliance, so IT should work with the other functions, mentioned above, to ensure appropriate compliance coverage.
Cloud compliance resources common to the top three providers include:
- Cloud Internet Service Providers in Europe (CISPE) – a non-profit that promotes high-level security and data protection.
- Clarifying Lawful Overseas Use of Data Act (CLOUD Act) a U.S. federal law enacted in 2018.
- Center for Internet Security (CIS) Benchmark – configuration guidelines to safeguard against cyberthrheats.
- Criminal Justice Information Services (CJIS) – a set of recommendations for cloud computing by law enforcement, national security and the intelligence community.
- Cloud Security Alliance (CSA) – best practices.
- Cyber Essentials Plus – certification by the U.K.’s National Cyber Security Centre
- Family Educational Rights and Privacy Act of 1974 (FERPA) – a United States federal law that governs the access to educational information and records by public entities including potential employers, publicly funded educational institutions, and foreign governments.
- EU-US Privacy Shield – a data protection framework.
- Federal Risk and Authorization Management Program (FedRAMP) – security standard certification
- Federal Information Processing Standards (FIPS) – a U.S. government computer security standard used to approve cryptographic modules.
- General Data Protection Regulation (GDPR) – the EU’s Privacy Shield replacement which went into effect in 2018.
- G-Cloud – a framework that simplifies the procurement of technology products and services by U.K. government entities.
- Health Insurance Portability and Accounting Act (HIPAA) – guidance for protection of health information in cloud systems.
- ISO 9001 – the international standard for a quality management system (QMS)
- ISO 27001 – an international standard that specifies the requirements for establishing, implementing, maintaining and continually improving an information security management system within the context of the organization.
- ISO 27017 – an international standard that provides guidelines for information security controls applicable to the provision and use of cloud services.
- Multi-tier Cloud Strategy (MTCS SS584) – a Singaporean standard for sound risk management and security practices, transparency and accountability.
- Motion Picture of America Association (MPAA) – best practices for content security.
- My Number Act – The 2016 enactment of a Japanese 12-digit personal identification number system.
- National Institute of Standards and Technology (NIST) 800-53 – a catalog of security and privacy controls for federal information systems.
- Payment Card Industry Data Security Standard (PCI DSS) – a standard that includes 12 requirements for any business that stores, processes or transmits payment cardholder data.
- Securities and Exchange Commission (SEC) Rule 17-a – a broker-dealer data preservation regulation.
- Systems and Organizations Control (SOC) 1 – a report on controls at a service organization that may be relevant to user entities’ internal control over financial reporting.
- Systems and Organizations Control (SOC) 2 – a report that evaluates an organization’s information systems relevant to security, availability, processing integrity, confidentiality or privacy.
- Systems and Organizations Control (SOC) 3 – a report, that unlike SOC 2, does not detail the testing performed and is meant to be used as marketing material.